We're getting everything ready for you...

Hey, Microsoft 365 admins! You are the one holding the keys, keeping your company’s digital world safe from hackers. With threats such as phishing emails, malware, and data leaks constantly emerging, securing your Microsoft 365 setup is now a significant concern for you.
In this blog post, we explore the top security settings you should know in 2025 to protect your data, ensure compliance, and keep your organisation safe. Additionally, there are some new changes this year that you need to be aware of.
Microsoft 365 is like the heart of your workplace. As you know, powerful tools such as Teams, Outlook, SharePoint, and OneDrive help you collaborate smoothly. However, since it’s in the cloud, it’s a big target for cybercriminals. If you fail to protect it, your sensitive information could be stolen, and you might face consequences related to regulations like GDPR or HIPAA. As an admin, you’re the one who keeps everything secure, and these settings will help you protect your data and keep things running. You can also take Microsoft Office 365 courses online to keep your account more secure.
Here are the 14 best security settings we should use in 2025. Each one is simple to set up, and we’ll explain why it’s so helpful.
MFA makes users prove it’s really them with a code. It’s like adding an extra lock to your door. You can authenticate by multiple methods, such as a mobile app, calling or text messaging. Also, you can create a password for apps that do not support MFA. It’s one of the most effective ways to prevent unauthorised access, especially as it will keep Microsoft 365 secure from phishing attacks. Research suggests it stops over 99% of hacker attacks.
Tip: New setups might have MFA on by default with security defaults, also use the Microsoft Authenticator app for more flexibility.

The principle of least privilege (POLP) is the basic idea behind giving administrators only the access they need to do their job. RBAC makes sure people only get access based on their role. For example, a helpdesk employee shouldn’t have global admin access, they can do their job with a user admin or helpdesk role. So, if your account gets hacked, it limits the trouble they can cause. You can use the Directory Reader role, which enables the app to read all user accounts.
How to do it:
You can assign specific roles here.
Tip: Use Azure AD’s built-in roles to simplify permission management.
Conditional Access in Azure Active Directory (Azure AD) allows you to control who can log in based on where they are or what device they use. For example, you can require multi-factor authentication (MFA) for users accessing sensitive apps from untrusted networks.
Tip: Start with one rule and test it so you don’t lock anyone out.

You should do everything to stop anyone from getting into your Microsoft 365 system without permission, and you also need to be ready in case someone does get in. Audit logs just work like a security camera for you, they will help you to track what everyone does, logins, and file shares, helping you to spot weird stuff and follow rules like HIPAA, which may require longer log retention.
Tip: Look at logs weekly for anything strange, like logins from unfamiliar locations.
You know what, preset Security Policies are Microsoft’s ready-made rules to stop spam, malware, and phishing emails. They also offer you Standard and Strict templates to keep your Office 365 mail secure. And the benefit of using these templates over manually created policies is that they update on their own to stay strong, and they defend your Exchange Online environment from the newest attack patterns.
without creating any hassle for you.
And now you can apply the Standard or Strict template for anyone you want.
Tip: If you have Microsoft Defender for Office 365, you can adjust these for extra protection.
As an admin account, your account has more privileges, and hackers usually make it a prime target for attack. So, you need to keep them extra safe to prevent widespread damage. You can secure them by enabling MFA, using strong and unique passwords, and limiting the number of admin accounts. You can implement Privileged Identity Management (PIM) in Azure AD to provide just-in-time access, reducing the risk of standing privileges. And always monitor admin activity logs for suspicious behaviour and restrict admin access to trusted IP ranges where possible.
Tip: You can follow Microsoft’s guidance to keep emergency account passwords in a safe place, like a locked drawer.

You might know that old login methods don’t work with MFA, and hackers can easily connect only with the username and password, and they can get it through a phishing email attack. Microsoft is turning off legacy Exchange Online tokens, but before you disable them, you should verify that your business applications or your users are not using any protocols.
Tip: Make sure everyone uses apps like Outlook or Teams to avoid disruptions.
SharePoint and OneDrive both have a feature in which end users can easily share their documents with a user who is not a part of your company if it is allowed. However, you have to keep in mind that loose sharing can let files get into the wrong hands sometimes. So, you may think for some time and make some rules to stop leaks.
Tip: Use Data Loss Prevention to watch file sharing.
Data Loss Prevention (DLP) policies will help you identify and protect sensitive information, like credit card numbers, personally identifiable information (PII) or health records, and stop it from being shared unsafely.
In Microsoft Purview,
You can make a policy to warn users about sharing or detecting sensitive data and set actions like blocking or notifying users. Start with Microsoft’s default DLP policies.
Tip: Test DLP policies in audit mode before enforcing them to avoid user disruption.
If you choose to use Microsoft Defender, it would be great for you because Defender will provide you with advanced threat protection, including anti-phishing, Safe Links, and Safe Attachments. Preset Office 365 security policies that use suggested settings to safeguard users and workloads in your environment are included with all Microsoft 365 subscriptions.
In the Microsoft Defender Portal,
Tip: Check threat reports regularly to stay ahead.
People can make mistakes, like clicking on bad links. Training helps everyone stay careful. So, try to conduct meetings and training to create awareness among employees. Especially employees who are new individuals and don’t have any idea about the dangers of social engineering tricks and phishing emails. Teach them how to make strong passwords and educate them on the basics to stay safe, because cyber threats are becoming smarter day by day, and it is important to keep reminding users to stay alert and report anything that looks strange. You can do this by sending regular emails or by conducting training to keep them up to date.
while using Office 365 email.
Tip: Update training to cover new tricks, like fake emails made by AI.

Think of updates like a shield for your Microsoft 365 apps. Old software can have holes that are like an open door for hackers. So, regularly updating Microsoft 365 applications, operating systems, and related software is essential to protect against vulnerabilities. But you are worrying about when to update? Don’t worry, Microsoft will send updates to fix weak spots, so don’t skip them. Turn on automatic updates for your apps and make sure devices use the latest versions of Windows.
Tip: Watch for Microsoft’s alerts about important updates.
Alert Policies are turned on by default in your Microsoft Office 365 property. Alert Policies tell you about weird stuff, like strange logins or big file uploads or any activities that are suspicious to alert you, so you can fix it fast and safe yourself from any data loss incidents.
Tip: Focus on big risks, like admin account changes.
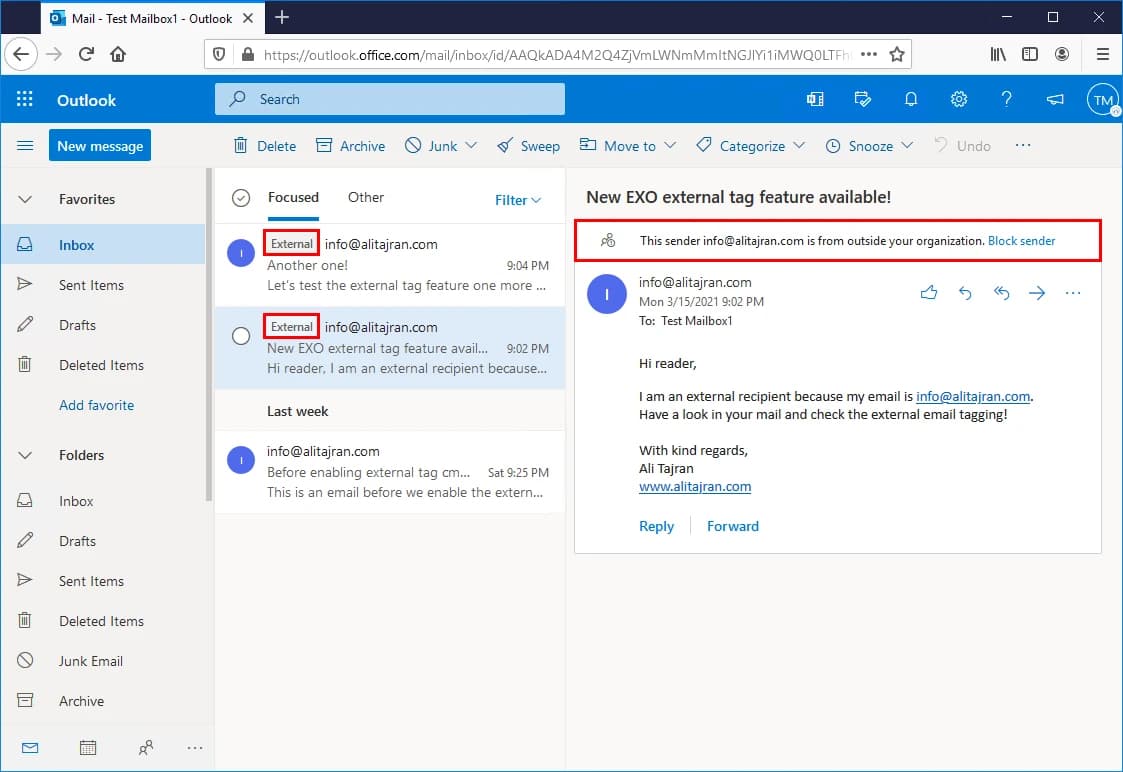
Tagging external emails helps your team spot them. It's a newly launched feature where you can tag external emails with more security to increase your users' awareness of the email's source. It lowers the chance of falling for phishing.
Tip: Tell everyone to check external emails carefully.
Microsoft is making some big changes in 2025 that we need to know about:
Microsoft is also adding new tools like Microsoft Entra ID Governance for managing access and Microsoft Defender for Business for endpoint security.
Being a Microsoft 365 admin is a big job, responsibility, and you are up for it. By using MFA, setting up RBAC, adding conditional access, and tapping into tools like Defender and DLP, you are keeping our data safe. So, let’s check audit logs, update software, and train your team to stay ahead of hackers. With 2025’s changes, you need to stay sharp and adapt.



August 4, 2025

August 1, 2025


July 27, 2025